Historically, IT departments in enterprises have managed centralized data centers. All data would funnel into these hubs to be processed, analyzed, and stored. But, with the rapid deployment of IoT devices, such a centralized approach becomes less feasible. Transmitting vast amounts of data from geographically dispersed devices to a central location introduces latency, costs, and potential security vulnerabilities.
As we dive headfirst into a new age of technology, two buzzwords keep floating around—IoT and edge computing. You’ve likely heard these terms more times than you can count. But what do they really mean for the future of IT?
Related blog: From legacy to leading-edge: 7 ways to strengthen the IT backbone of FinOps in 2024
Let’s unpack this transformation.
Edge Computing and IoT: Transforming enterprise-grade IT Ecosystems
Edge computing and IoT technologies are helping enterprises deal with increasingly complex IT ecosystems while improving real-time decision-making and reducing operational costs.
Real-time insights
Traditional centralized data models, where information is sent to far-off data centers for processing, often introduce latency, muddying the waters of real-time analysis. Edge computing, however, processes data at or near its source —be it sensors on a production line, smart cameras in retail spaces, or wearables in healthcare.
This proximity triggers instantaneous feedback, allowing businesses to react in real-time to any operational anomalies or to optimize processes on-the-fly.
Efficiency and cost benefits
IoT devices, from environmental sensors to connected systems, generate vast amounts of data. Transmitting this data continuously to centralized data centers isn’t just slow; it’s expensive and consumes significant bandwidth. By integrating edge computing, enterprises can filter and process data locally, transmitting only what’s essential. It reduces transmission costs and alleviates network congestion, making the IT ecosystem more efficient.
Infrastructure flexibility
As businesses expand, so does their data and device footprint. Edge computing offers a decentralized model, enabling enterprises to scale out by merely adding more edge devices without overhauling their central infrastructure. This modular approach provides unprecedented flexibility, allowing businesses to adapt and expand their IT ecosystems in alignment with changing operational demands.
Related blog: Lead through change: An IT manager’s guide to digital transformation
Integration of IoT and edge computing with IT existing systems

Integrating IoT and edge computing with existing IT systems predominantly hinges on deploying gateways and specific communication protocols. Gateways function as intermediaries, facilitating seamless communication between edge devices and centralized IT infrastructures. They handle data filtration, protocol translation, and preliminary data analysis so that only pertinent data is relayed to the central system, thus optimizing bandwidth utilization.
For seamless communication, lightweight messaging protocols like MQTT and CoAP are employed, tailored for the specific demands of constrained devices and low-bandwidth environments.
Concurrently, device management platforms oversee the vast array of IoT devices, managing tasks such as device authentication, firmware updates, and configuration. API interfaces are important in this integration, enabling the diverse software components to interact. Lastly, data normalization processes are imperative to standardize the data from various IoT devices, enabling consistent processing and analytics within existing IT systems.
So, integrating edge computing and IoT brings positive shifts in the IT environments. However, knowing the implications and challenges one may face in this journey is important.
Infrastructure implications of edge computing and IoT
The surge in IoT devices directly translates to a need for a scalable infrastructure. Enterprises must prepare to support thousands or billions of interconnected devices.
Additionally, the move to edge computing makes managing these devices more challenging. Instead of overseeing a centralized system, IT teams must manage data processing across countless edge locations. This decentralization necessitates new, precise management and monitoring tools tailored for such dispersed architectures.
Furthermore, the spectrum of IoT devices introduces variability in hardware. Each device’s unique hardware profile requires distinct configurations and oversight methods. For IT departments, this means adapting and diversifying their approach to hardware management, ensuring each device integrates smoothly into the broader IT ecosystem.
Security challenges of edge computing and IoT
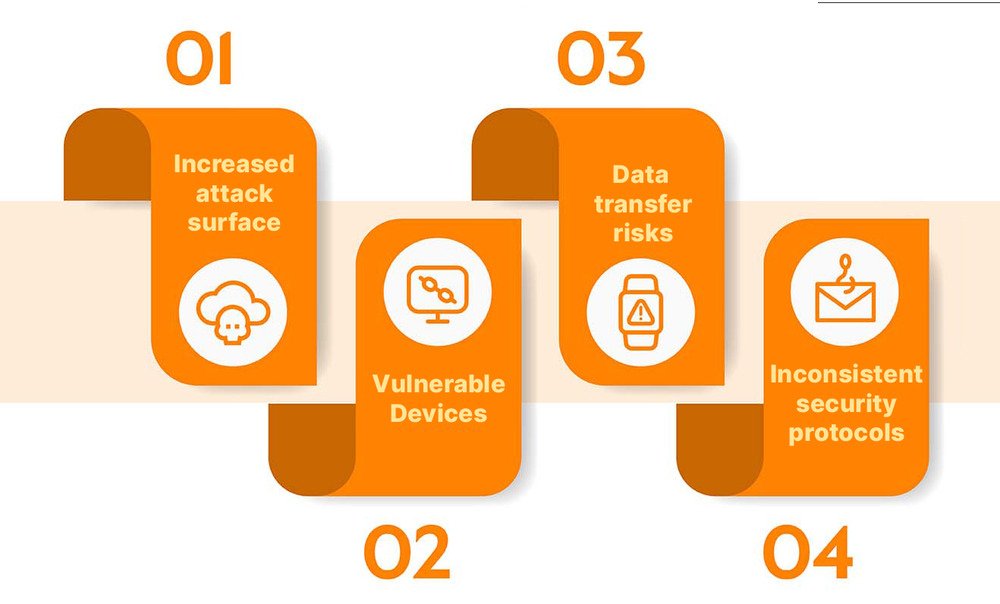
Increased attack surface
With the integration of countless IoT devices and the shift to decentralized edge computing architectures, IT ecosystems face an expanded attack surface. This growth means more potential entry points for cyber threats, necessitating enhanced security measures and vigilant monitoring to safeguard the enterprise’s digital footprint.
Device vulnerabilities
A concerning aspect of IoT adoption is the inconsistent security standards across devices. Many IoT devices, especially earlier or cheaper models, may not prioritize robust security features. As these devices get incorporated into IT networks, they can pose significant risks, acting as weak links that malicious entities might exploit.
Data transmission risks
While edge computing processes a substantial amount of data locally, a portion always needs to be transmitted, be it for centralized storage or further analysis. Even if reduced compared to traditional models, this act of transmitting data presents its vulnerabilities. Ensuring this data’s encrypted and secure transfer is paramount to prevent potential interceptions or breaches.
Inconsistency in security protocols
As enterprises expand their IT networks with many IoT devices from manufacturers, maintaining a consistent security protocol becomes challenging. Devices may have different update cycles, security patch rollouts, and inherent vulnerabilities. Ensuring that each device adheres to a standardized security framework and is consistently updated to defend against emerging threats becomes a significant operational challenge for IT teams.
Related blog: Stress-free IT management: An IT manager’s playbook for mitigating risks
How to prepare IT teams to maximize edge computing and IoT
The rise of edge computing and IoT will likely greatly impact the IT world. Hence, enterprises must make sure their teams are ready to overcome challenges and capitalize on the opportunities. Here are three major focus areas:
Skill development
IT teams must undergo comprehensive training in the fundamentals of edge computing and IoT device management. Understanding security protocols and best practices tailored to these new environments becomes vital. This knowledge equips them to tackle unique challenges and vulnerabilities associated with decentralized data processing and a myriad of interconnected devices.
Collaborative approaches
The era of siloed operations is becoming obsolete, especially in an IoT-driven environment. IT teams can no longer operate in isolation. A collaborative approach is required, particularly with security teams.
Given the deeply connected nature of operations and security in these new ecosystems, creating a symbiotic relationship ensures that vulnerabilities are quickly identified and addressed, and operational standards are maintained without compromising security protocols.
Tool familiarity
IoT and edge computing technologies have led to the emergence of new tools designed for monitoring, management, and analytics specific to these domains. Regular workshops, hands-on training sessions, and sandbox environments can aid in familiarizing IT personnel with the latest tools so that the enterprise remains agile and responsive to the evolving technological landscape.
Related blog: The Next Big Thing in SaaS IT Operations Management
Conclusion
In summary, the convergence of IoT and edge computing technologies is reshaping the future of IT ecosystems in profound ways. This transformative shift promises to empower enterprises with real-time insights, efficiency gains, and unprecedented flexibility. Edge computing, by processing data at or near its source, enables instantaneous feedback and responsive decision-making, reducing operational costs and enhancing overall efficiency. The integration of IoT with edge computing is not without its challenges, such as the need for scalable infrastructure, precise management tools, and robust security measures. However, with careful preparation, skill development, collaborative approaches, and familiarity with the latest tools, IT teams can overcome these challenges and seize the opportunities presented by this new era of technology.
As we move forward, it is imperative for enterprises to embrace this technological evolution and equip their IT teams with the knowledge and skills necessary to navigate the complex landscape of IoT and edge computing. By doing so, organizations can harness the full potential of these transformative technologies, ensuring their competitive edge and adaptability in an ever-evolving digital world.