The pandemic may have accelerated the need for enterprises of all sizes to move towards digital transformation, but the need for zero trust cyber security has existed since before. However, with new actors or hackers, malicious software has also evolved and expanded the cyber threats to a larger attack surface.
While enterprises need robust digital solutions, implementing them may make your enterprise more vulnerable to security threats. Still, cyber security remains paramount as, without that, your business stands little to no chance of retaining its position in the marketplace. Similarly, only MSPs who include strong security measures can maintain their standing. Therefore, adopting Zero Trust in MSPs becomes imperative.
Zero Trust, and why is it essential in today’s digital era?
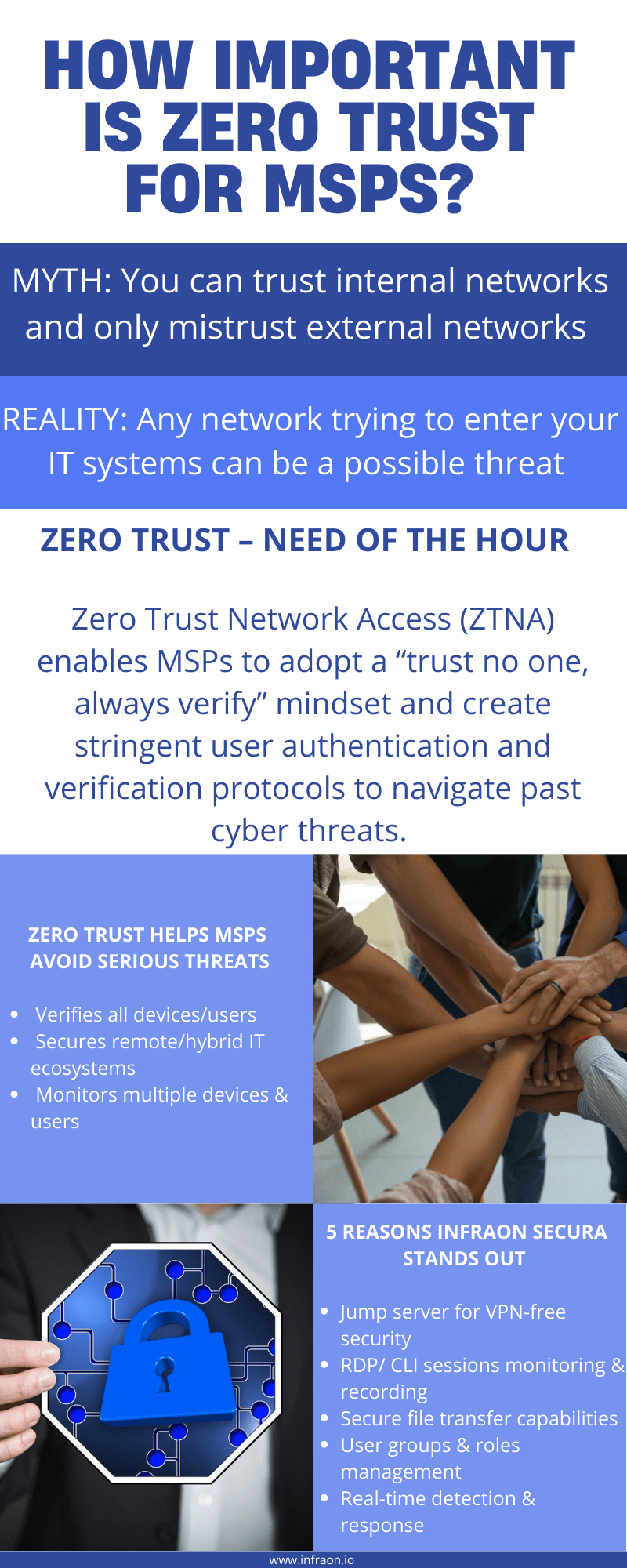
The theory that you can trust internal networks and mistrust only the external networks doesn’t hold water anymore because of the rising security threats. Any network trying to connect to your IT systems must be viewed as a possible threat. Since enterprises find themselves relying on MSPs for various applications and virtual network services, an MSP that comes with inherent ZTNA has an edge.
The concept of Zero Trust architecture is that trust is not a given regardless of accounts or devices because of their location, i.e., each user or device must be authorized and verified on as granular a level as possible.
Essentially, the Zero Trust model assumes that no device or user can be trusted until verified. This approach includes access to internal networks, especially as more enterprises have become cloud-based and mobile. Therefore, enterprises need to define who can be trusted among internal users, vendors, contractors, and customers. Only when verified any user may be given access to the network.
With employees working from remote locations, their need to access the company network needs particular scrutiny and continued monitoring. Only a remote access software can monitor multiple devices and users simultaneously while ensuring that the employees can securely connect with each other and the network.
Leverage the expertise of MSPs to implement ZTNA for your enterprise.
MSPs can analyze your enterprise and incrementally implement the foundation of Zero Trust even as they set up processes to monitor and manage your network and systems.
Implementation of the Zero Trust framework through an MSP
MSPs can give you a global on-demand private network that you can use to scale up or down your enterprise without adding new infrastructure. They can implement the least-privilege access model of Zero Trust, where only securely identified and authorized connections are allowed access to your network.
Moreover, MSPs are in a position to implement the Zero Trust model without causing any disruption in productivity. For ZTNA to work, all you need is remote computer access software, access to the network, and internet connectivity. The Zero Trust remote access software uses secure technology, ensuring access only after identification or authentication.
MSPs can manage the changes needed for Zero Trust from outside the enterprise while the synergy between your teams is undisturbed. They can control the transition to a new model without disrupting daily operations or productivity.
Cost-effective Zero Trust solutions through an MSP
Using an MSP to implement your ZTNA is cost-effective. Implementing security measures on your own will cost time, resources, and finances thats also take away from the functioning of your enterprise. MSPs’ knowledge base is established, and they have the technology and experience to provide secure solutions uniquely designed to meet your security needs. MSPs offer different packages that your enterprise can use depending on your budget.
Enterprises that seek digital transformation to keep pace with the evolving demands of Industry 4.0 are looking for solutions and service providers that go hand-in-hand with robust security. It can often be difficult for enterprises to implement adequate security independently. Therefore, relying on an MSP to cater to security needs can significantly speed up the process of digital transformation. This is where Infraon’s SecuRA comes in.

Infraon SecuRA to ensure comprehensive security for your enterprise
SecuRA is engineered as a remote and secure framework to protect your applications even as it ensures access is only for authenticated and authorized users and devices. Infraon SecuRA is a remote access platform to empower detection and response in real-time, with centralized policies and Zero Trust features. The unique features of SecuRA include:
- User/application authentication, device authentication, and trust/ policies
- A gateway-based system that enables secure connection without VPN
- Integrate RDP/ VNC and CLI
- RDP/ CLI sessions monitoring and recording
- Secure file transfer capabilities
- Session monitoring and management
- Monitor and manage device inventory, authorization, and authentication.
- Monitor web-based applications
- User groups and roles management
- Zero Trust security to restrict potential threats by unauthorized users.

To conclude
A successful product or service delivery is impossible without total security, so it is time for enterprises to leverage ZTNA technologies to enable application access without going through the network. The Zero Trust model is a game-changer as it is completely based on identities and devices, with authorization always coming first. This is what we call the Zero Trust advantage for network security.