How do computer systems, servers, routers, switches, and other network-enabled devices communicate without protocols? Without these protocols, how would devices interpret the electronic signals exchanged over network connections?
Have you ever considered protocol and how the network operates? How often do you rely on network protocols without realizing it? Network protocols function seamlessly whenever you connect to the Internet, send an email, or make a phone call. Although their specific operations may not be immediately apparent, they are integral to enabling internet access and facilitating digital communication.
Related article: What is Network Performance Monitoring?
Let’s explore the concepts and workings of network protocols and a comprehensive list of them to help you understand their crucial role in modern digital communications.
What is Network Protocol?
A network protocol is a set of rules that dictate how devices on a network communicate and govern how data is formatted, transmitted, and received. These protocols ensure that devices can understand and process information exchanged between them, making communication possible between computers, servers, routers, switches, and mobile phones.
A network protocol defines devices’ communication, including when to transmit data, error handling, and data formatting. It ensures smooth communication by specifying packet structure, addressing, error-checking, and security. Network protocols act like traffic signals, regulating data flow to prevent errors and support multiple destinations or continuous streams.
How Does Network Protocols Work?
A network protocol establishes rules defining how data is transmitted and received between devices on a network. Here’s how it works step by step:
- Data Packaging: The data to be transmitted is divided into small units called packets. Each packet contains data, metadata such as source and destination address, and sequencing information for reassembly.
- Transmission: Once the data is packaged, the network protocol defines how the packets are transmitted. For example, IP (Internet Protocol) determines the addressing and routing of the packets to ensure they reach the correct destination device.
- Error Checking: To ensure data is not corrupted during transmission, protocols like TCP (Transmission Control Protocol) check for errors. A packet is retransmitted to ensure reliable communication if lost or corrupted.
- Reassembly: Once the packets reach their destination, the protocol ensures they are reassembled correctly to form the original data. TCP ensures packets are delivered in the proper order, while HTTP/HTTPS presents the data to an application, like a web browser.
- Acknowledgment: The receiving device may return an acknowledgment to the sender to confirm successful receipt. The protocol can trigger a retransmission request if there is any issue, such as missing or corrupted data
Network protocols provide the rules and steps that ensure data is correctly packaged, transmitted, checked for errors, and reassembled, enabling reliable communication between devices on a network.
They also include extra information that makes network connections more reliable and efficient, such as checksums that help network applications detect data corruption or manipulation and counters that keep track of the order in which communications were sent. The data to be transferred is included in the payloads portion.
Network Protocols and the OSI Model Explained
While network protocols follow a similar structure, each has unique rules its developer defines. Understanding the Open Systems Interconnection (OSI) model, a foundational framework for most protocols, is essential for grasping these differences. The OSI model breaks communication into seven independent layers, each handling specific tasks during data transmission.
The seven layers of the OSI model are used to divide the communication between two network devices. Each of these seven layers is given a set of tasks and each layer is independent of the others, allowing each to independently do its duties. Here is an illustration of the communication process between two network devices using the OSI model to bring this into context.
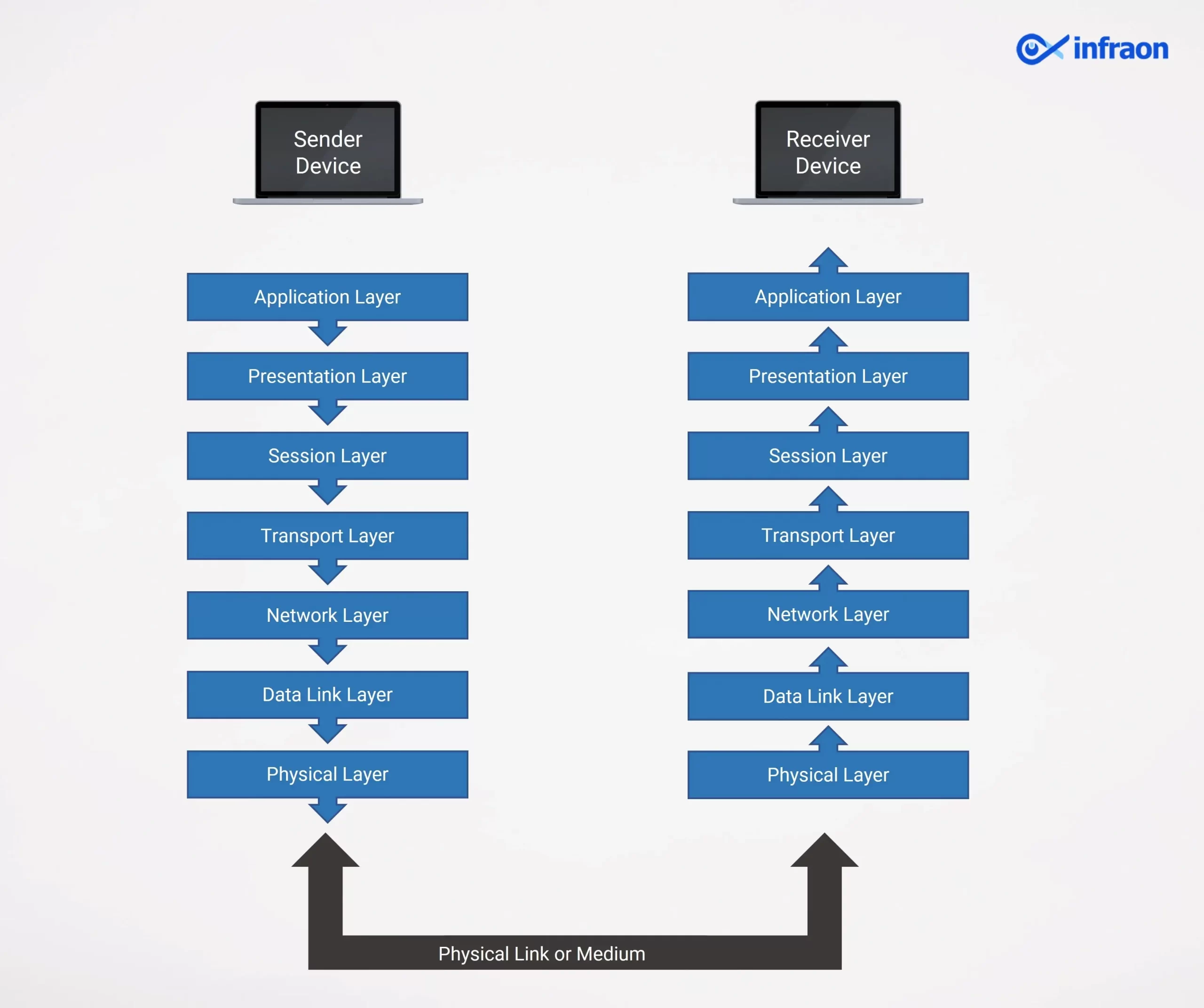
Let’s look at the detailed descriptions of the functioning of network protocols in each layer of the OSI model:
- Application Layer: This is the top layer where end-user applications operate. It directly interacts with software like web browsers (e.g., Chrome), email clients (e.g., Outlook), and other services to provide network-related services. This layer handles user-facing protocols like HTTP for web browsing and SMTP for email sending.
- Presentation Layer: The Presentation Layer is responsible for translating, encrypting, and compressing data. It ensures that data sent from the application layer is in a format the receiving device can understand. This layer handles data transformations like converting between different character encoding formats (e.g., ASCII to Unicode), data encryption for security (e.g., SSL/TLS), and compression to reduce data size.
- Session Layer: The Session Layer manages sessions or connections between two communicating devices. It establishes, maintains, and terminates communication sessions. For instance, it ensures that a connection between a web browser and a server is adequately established, maintained throughout the interaction, and properly closed after the communication ends.
- Transport Layer: This layer ensures reliable data transfer by breaking it into smaller packets, providing error correction, and managing flow control. It is responsible for end-to-end communication and error recovery. Standard protocols at this layer include TCP (Transmission Control Protocol), which ensures data is delivered in the correct order and without errors, and UDP (User Datagram Protocol), which offers faster, less reliable transmission.
- Network Layer: The Network Layer is responsible for routing data across different networks. It handles addressing (e.g., IP addresses) and determines the best path for data to travel from the source to the destination. IP (Internet Protocol) operates at this layer, ensuring that data is routed correctly across different networks to its intended destination.
- Data Link Layer: The Data Link Layer ensures that data is transferred reliably between two devices on the same network segment. It handles the physical addressing of devices (e.g., MAC addresses) and error detection to ensure data integrity. Protocols like Ethernet and Wi-Fi operate at this layer, facilitating communication between devices on a local network.
- Physical Layer: The Physical Layer transmits raw binary data (1s and 0s) over the physical medium, such as cables, fiber optics, or wireless signals. This layer defines the hardware elements involved in data transfer, including electrical signals, radio waves, and connectors. It ensures that data is physically transmitted between devices.
The OSI model’s seven layers work together to facilitate communication between devices, with each layer handling a specific task. Data starts at the Application Layer, moves through the layers during transmission, and is reassembled on the receiving device. The OSI model helps clarify how protocols interact and manage data exchange.
Types of Network Protocols
Network protocols are essential for ensuring effective communication, management, and security within networks. They define the rules and conventions devices follow to exchange data, manage network resources, and secure information. Network protocol and its types can be categorized into three main types:
1) Network Communication Protocols:
These protocols enable communication between devices on a network and ensure that data is transmitted correctly and efficiently. Communication protocols handle how data is packaged, addressed, and transferred across a network.
- Transmission Control Protocol (TCP): Ensures reliable, ordered data delivery between devices.
- Internet Protocol (IP): Handles the routing of data packets across different networks.
- User Datagram Protocol (UDP): A connectionless protocol for low-latency communications like streaming and gaming.
- Hypertext Transfer Protocol (HTTP): Used for web communication, enabling browsers to request and display web pages.
- File Transfer Protocol (FTP): Transfers files between client and server over a network.
- Simple Mail Transfer Protocol (SMTP): Governs the sending of email messages between mail servers.
- Post Office Protocol (POP3) / Internet Message Access Protocol (IMAP): Retrieve emails from a server. POP3 downloads messages, while IMAP stores them on the server for flexible access.
2) Network Management Protocols:
These protocols monitor, manage, and troubleshoot network devices and their performance. They help administrators optimize network operations and ensure everything runs smoothly.
- Simple Network Management Protocol (SNMP): Monitors and manages network devices by collecting data and sending configuration commands.
- Dynamic Host Configuration Protocol (DHCP): Automatically assigns IP addresses to devices on a network.
- NetFlow: Collects and analyzes network traffic data to monitor performance and detect issues.
- Internet Control Message Protocol (ICMP): Used for diagnostics (e.g., ping command) to check device availability and network performance.
- Network Time Protocol (NTP): Synchronizes clocks across devices in a network for accurate logging and event tracking.
- Common Management Information Protocol (CMIP): This advanced protocol, which offers more extensive features than SNMP, is used in larger networks to manage and monitor devices.
3) Network Security Protocols:
Secure network connection protocols ensure the confidentiality, integrity, and authenticity of data transmitted over a network. They protect data from unauthorized access and cyber threats.
- Secure Sockets Layer (SSL) / Transport Layer Security (TLS): These protocols encrypt secure web communication and protect sensitive data during transmission.
- Internet Protocol Security (IPsec): Secures communication by encrypting IP packets and ensuring secure VPN connections.
- Secure Hypertext Transfer Protocol (HTTPS): An encrypted version of HTTP, ensuring secure communication between web browsers and servers.
- Secure Shell (SSH): Provides secure remote access to network devices and systems.
- Wi-Fi Protected Access (WPA2 / WPA3): Secures wireless networks by encrypting data and providing strong authentication.
- Pretty Good Privacy (PGP) / GNU Privacy Guard (GPG): Used to encrypt and secure email messages, ensuring privacy between the sender and recipient.
- Kerberos: A network authentication protocol that securely verifies the identities of users and devices in a network.
These network protocols are crucial for network systems’ smooth and secure operation. They provide structured communication, effective management, and robust security, ensuring the reliability and safety of data transmission across diverse networks.
Related Article: Types of Network Performance Monitoring Tools
Challenges in Network Protocol Implementation
Implementing network protocols is crucial for ensuring seamless communication across devices and networks. However, it is not without its challenges. Below are some key issues organizations face during network protocol implementation:
- Compatibility Issues: Ensuring seamless communication between devices using different protocols or legacy systems can lead to integration challenges, especially in diverse network environments.
- Security Vulnerabilities: Outdated or misconfigured protocols, such as FTP or older versions of SSL, can create significant risks by exposing networks to cyberattacks and data breaches.
- Scalability Concerns: Managing protocols in large-scale networks with growing numbers of devices and heavy data traffic can strain resources and reduce efficiency.
- Complex Configurations: Configuring and maintaining protocols like IPsec or SNMP requires advanced expertise, which increases the likelihood of errors and makes implementation time-consuming.
- Performance Bottlenecks: Inefficient or outdated protocols can lead to slow data transfer, network congestion, and increased latency, negatively impacting overall performance.
How to Overcome Network Protocol Implementation Challenges?
To address these challenges effectively, organizations can:
- Standardize Protocols: Adopt widely accepted standards to enhance compatibility and interoperability.
- Leverage Automation: Using automation tools for protocol configuration and network management to reduce human errors.
- Invest in Training: Equip network administrators with the necessary skills to handle complex configurations and updates.
- Monitor Networks: Regularly monitor network performance and security to identify and address issues early.
- Stay Updated: Ensure protocols are updated with the latest security patches and standards.
By addressing these challenges, organizations can create efficient, secure, and scalable network environments.
Top 7 Examples of Network Protocol Uses
- Web Browsing (HTTP/HTTPS): This protocol enables the loading of web pages and ensures secure browsing through encrypted communication.
- Email Communication (SMTP, IMAP, POP3): This protocol facilitates sending, retrieving, and managing emails efficiently over the Internet.
- File Transfers (FTP/SFTP): FTP transfers large files between devices, and SFTP adds encryption for secure transfers.
- Video Conferencing (RTP, SIP): Powers seamless video and audio communication for tools like Zoom or Microsoft Teams.
- Network Monitoring (SNMP): Administrators can monitor and manage network device performance and health.
- Internet Connectivity (TCP/IP): This protocol forms the foundation of data exchange over the Internet, ensuring reliable and accurate transmission.
- Secure Transactions (SSL/TLS): This protocol protects sensitive data, such as payment information, during online banking and e-commerce.
Key Roles of Infraon NMS in Network Protocol Management
- Network Protocol Monitoring & Analysis: Infraon NMS continuously tracks network protocols, ensuring optimal performance and providing detailed data on usage, performance, and potential issues. This analysis allows network administrators to make informed decisions to enhance network operations. Ready to experience it. Schedule a Demo
- Network Protocol Configuration Management: Infraon NMS simplifies the configuration and management of network protocols like VPNs and VLANs. It ensures that devices communicate seamlessly, enabling smooth data transfer and efficient network operations.
- Security Management for Network Protocols: By actively monitoring suspicious activity and ensuring adherence to security policies, Infraon NMS identifies and mitigates security risks associated with network protocols, enhancing your network’s security posture.
- Fault Management in Network Protocols: Infraon NMS detects and diagnoses protocol-related faults in real-time, providing immediate alerts and automated actions to minimize network downtime and ensure consistent reliability.
Benefits of Infraon NMS for Network Protocols:
- Enhanced Network Performance: Infraon NMS optimizes network protocol configurations, improving network efficiency and reducing latency, ensuring reliable data transfer and high performance.
- Improved Security Continuous monitoring of network protocols and proactive threat detection helps safeguard your network from potential security breaches, ensuring your organization remains protected.
- Reduced Downtime: Real-time alerts and fault management minimize downtime, ensuring your network remains available and services run smoothly without interruptions.
- Scalable Solution: Infraon NMS supports network growth, providing the flexibility needed for businesses to scale their infrastructure as operational demands increase.
- Compliance and Reporting: With detailed reporting and audit trails, Infraon NMS simplifies compliance with industry standards, making it easier to meet regulatory requirements.
Final Note
Infraon NMS offers a scalable feature for managing network protocols, ensuring optimal security, performance, and reliability. It helps businesses prevent network issues and optimize infrastructure for growth.
Network protocols are the foundation of modern communication, enabling seamless data exchange for internet access, secure transactions, and network management. Understanding protocols through frameworks like the OSI model ensures better connectivity, security, and performance. As networks evolve, optimizing protocols is key to supporting our connected world.
Ready to experience the benefits of Infraon NMS? Contact us today to unlock its full potential.
1) Which network protocol is used to assign IP addresses to network devices automatically?
This purpose is served by the Dynamic Host Configuration Protocol (DHCP), which allows devices to obtain IP addresses automatically when they connect to a network.
2) What does network protocol error mean?
A network protocol error occurs when the protocols that govern network communication malfunction or miscommunicate, causing devices to fail to exchange data properly or to interpret data incorrectly.
3) Which network protocol allows devices to communicate?
Transmission Control Protocol (TCP) and Internet Protocol (IP) are the fundamental protocols that enable devices to communicate over a network, ensuring reliable data transmission and routing between devices.