Every computer network relies on network devices to stay connected, secure, and efficient. These devices are the building blocks that make communication possible between systems, users, and applications. From small home setups to large enterprise data centers, understanding how different devices work helps IT teams design networks that are fast, reliable, and secure.
In this blog, we will explain what network devices are, their core functions, the different types of networking devices, and how they are used in real-world IT environments.
What Are Network Devices?
Network devices (also called networking devices or network components) are hardware or software elements that make it possible for data to move within and across networks. They enable routing, filtering, transmission, and security of data.
These devices can be physical, like routers or switches, or virtual, like cloud-based firewalls and software-defined routers. Every IT setup, whether in homes, enterprises, or data centers, depends on a mix of these devices to ensure smooth communication.
Functions and Uses of Networking Components
The main uses of networking devices include:
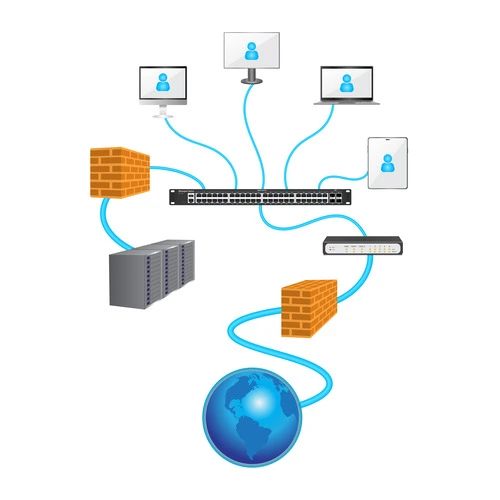
- Allowing communication across local (LAN) and wide (WAN) networks
- Managing and controlling data traffic to avoid congestion
- Boosting the speed, security, and reliability of data exchange
- Supporting scalability, segmentation, and connectivity in the ever-evolving IT sector.
From connecting employees in offices to powering cloud-based services, networking devices are critical to modern digital operations.
Related Blog: Network Topologies in Computer Networks
Common Types of Networking Devices and Their Functions
1. Repeater
A repeater strengthens and regenerates signals over long distances, preventing signal loss in large networks.
2. Hub
A simple device that broadcasts data to every connected device is a hub. It is being replaced by switches in modern setups, as it lacks intelligence.
3. Bridge
A bridge connects two LANs to form a larger network. It filters traffic and reduces collisions, improving efficiency.
4. Switch
Switches are smarter than hubs. They forward data only to the intended recipient and support full-duplex communication. This reduces traffic and improves performance.
5. Router
A router connects multiple networks and directs data packets based on IP addresses. It is essential for internet connectivity.
6. Gateway
It allows communication between networks that use different protocols or systems.
7. Brouter
A brouter combines the functions of a bridge and a router, handling both routable and non-routable protocols.
8. Network Interface Card (NIC)
A hardware component that connects a device to a network can be explained as a NIC. It can be wired or wireless.
9. Modem
A modem converts digital signals to analog (and vice versa). It enables internet access over phone or cable lines.
10. Wireless Access Point (WAP)
A WAP allows wireless devices to connect to a wired network. This expands mobility and flexibility.
Additional Network Components
Network Cables
Physical media such as Ethernet, coaxial, and fiber optic cables form the backbone of data transmission.
Transmission Media, Protocols, and Topology
These are essential network components that define how data moves, how devices communicate, and how networks are structured.
Virtual Network Components
In addition to physical devices, virtual devices like software-based routers, firewalls, and switches are now common in cloud and hybrid environments. Some of its benefits are flexibility, scalability, and cost efficiency. It is one of the best choices for modern enterprises.
Common Challenges in Network Device Management
Managing network devices can come with challenges such as

- Connectivity issues due to faulty cables or ports
- Hardware malfunctions leading to downtime
- DNS misconfigurations are disrupting access
- Overutilization or power fluctuations affecting performance
- Environmental issues like overheating due to poor ventilation
Best Practices for Managing and Securing Networking Devices
To keep networks reliable and secure, IT teams should:
- Regularly update device software and firmware
- Harden devices against unauthorized access
- Use VLANs to segment networks for better security
- Continuously monitor traffic and set alerts for anomalies
- Apply role-based access and strong user controls
- Document configurations and perform periodic audits
Companies like Infraon simplify these tasks by providing unified monitoring, control, and automation for both physical and virtual network Components.
Conclusion
Networking devices play a critical role in ensuring secure and reliable communication across IT infrastructures. From simple repeaters to advanced virtual devices, each has a unique function in supporting connectivity, scalability, and performance.
Organizations that invest in understanding and maintaining these network components are better equipped to avoid downtime, strengthen security, and enable smooth digital operations. Reviewing your current setup and upgrading where necessary is the first step toward building a future-ready network.
FAQ Section
Q1. What are networking components in simple terms?
They are hardware or software components that connect computers and systems, allowing data to be transmitted securely and efficiently.
Q2. What are the main types of networking devices?
Common types include repeaters, hubs, bridges, switches, routers, gateways, brouters, NICs, modems, and wireless access points.
Q3. What is the difference between a router and a switch?
A switch connects devices within a single network and directs traffic efficiently, while a router connects multiple networks and determines the best path for data to travel.
Q4. What are virtual networking components, and how are they used?
They are software-based versions of physical devices, used in cloud and hybrid environments for flexibility, scalability, and cost savings.
Q5. How can I secure my networking components from cyber threats?
Apply regular updates, use strong access controls, monitor network traffic, segment networks, and follow security best practices to reduce risks.