IT Asset
Management
Achieve higher ROI with Infraon’s IT
asset management solutions

Achieve higher ROI with Infraon’s IT
asset management solutions

IT Asset Management (ITAM) is a critical enabler for IT directors, heads, and managers looking to future-proof digital transformation initiatives. It encompasses the process of ensuring that IT hardware and IT assets are effectively accounted for, deployed, maintained, upgraded, and disposed of. Also, the asset records are maintained in the ITAM database.
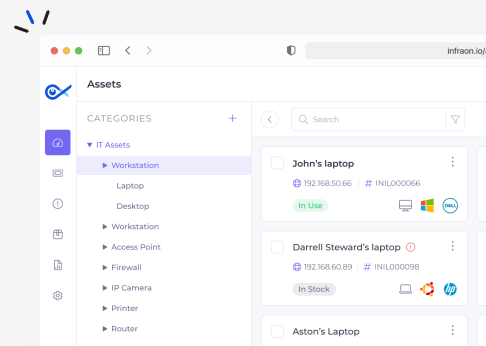
An effective IT asset management solution must equip teams to receive, tag, and maintain IT assets in a centralized inventory. That way, it becomes easy to track the end-to-end lifecycle.


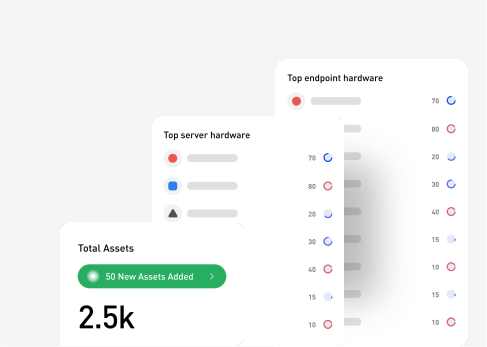
Infraon’s IT asset management solutions are equipped to manage end-to-end IT asset lifecycles - from requisitions and purchasing to retirement or disposal. Your users can track IT asset availability, health, and performance with an intuitive dashboard for spreadsheet-free visualizations.
Infraon also offers an agent-based and agentless IT asset management tool that can be customized based on your unique business needs. It comes with access to automated fault and incident management workflows.
Do more with your ITAM solution than before.
Optimize financial planning by accurately
depreciation – make informed asset-related decisions
Use a single solution to manage IT asset management lifecycles. Align IT decisions with business goals – starting from planning and acquiring to maintaining and retiring.
Easily track all physical IT asset components, such as laptops, desktops, servers, etc. Lower the total costs involved in enabling the smooth functioning of all related assets.
Centralize and manage the purchase, deployment, maintenance, and disposal of all your software assets. Mitigate security risks while reducing the time, effort, and costs involved.
Never lose sight of any of your IT asset needs. Track their real-time location status across teams, functions, regions, or premises.
Monitor the performance of IT asset vendors with real-time data. Avoid contract oversights and set KPIs with complete transparency.
Unify IT ticket management with an inbuilt ticketing system. Get multi-channel support with self-service options like chatbots, email-to-ticket, etc.
Track IT assets that are connected to the network – accessed by any business user. Smartly manage licenses and eliminate redundant costs.
Be instantly notified by low stock alerts and create a culture of IT asset availability. Prevent under-stocking that can cause business disruptions.
Gain control by ensuring the least privilege access privileges to IT assets. Use authentication and authorization protocols to stay clear of compliance risks.

Prebuilt Workflows
Customizable Reporting
User and Role Management
Audit Trails
Mobile Accessibility
Explore the impact of technological progress on IT asset management
and help future-proof your organization.

Continuously optimize the purchase, deployment, maintenance, and disposal of IT assets and their components in real-time without depending on multiple software.
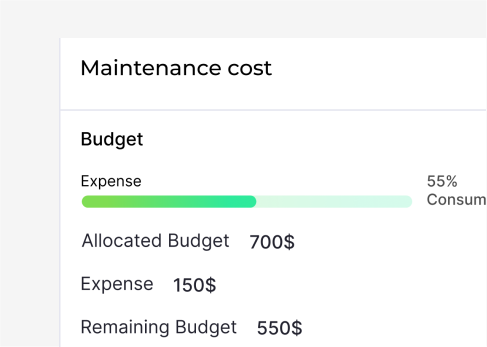
Effortlessly lower the overall costs of hardware asset management and software asset management without hiring expensive and certified resources.
Accurately monitor the performance of IT asset management software vendors to prevent any contractual oversights or shadow expenses.
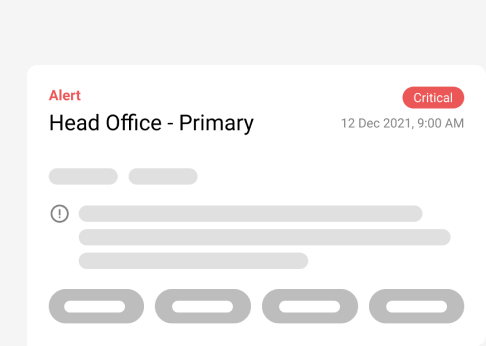
Seamlessly track and mitigate any security or compliance risks with actionable IT asset insights based on intelligent alerts and notifications.

Infraon's IT asset management solution is rooted in industry best practices such as:
Advanced data analytics to gain insights into IT asset performance, usage, etc.
Simplified identification, tracking, and reporting of IT assets
Integrated approach to tracking IT asset costs, depreciation, and ROI
Risk assessment to detect vulnerabilities and threats to the IT asset ecosystem
Tagging and tracking technologies like RFID to streamline inventory management
Change management procedures to manage modifications to IT assets
By deploying Infraon's IT asset management solution, you can enjoy benefits like:
Easier to incorporate green IT practices in asset management
Seamless collaboration between IT, finance, procurement, and other departments
Cost efficiency by accurately tracking and managing IT assets
Streamline IT operations through automated processes and centralized asset management
Reduced risk of legal penalties and enhanced data governance

IT Asset Management (ITAM) is a critical enabler for IT leaders to deliver digital transformation and cost optimization. It ensures that an organization’s assets are accounted for, deployed, maintained, upgraded, and disposed of when the time comes. The IT Asset management team receives hardware assets, tags them first, and keeps them in their inventory. It is tracked during the asset’s entire lifecycle, and the records are maintained in the IATM database.
Any business needs a robust Asset Management solution to ensure that all the purchased assets are tracked and accounted for seamlessly. When an employee raises a request for an asset, it is issued to them. When the employee separates from the organization and returns all the assets issued, the database is maintained with proper information. For BPO operations, the assets are assigned to the business unit, and they are made liable for their upkeep.
A powerful IT asset management solution has numerous advantages. Tracking of assets to ensure that there is no loss of equipment. It also helps centralize and manage the purchase, deployment, maintenance, and disposal of IT software components to mitigate the security risks and reduce time/effort/costs. The IATM engineer can monitor the performance of their IT asset management software vendors with real-time data.
IT Asset Lifecycle Management, IT Hardware Asset Management, Software Asset Management, Vendor Management, Location Management, Integrated Ticketing, Network Discovery, Agent-Based Discovery, and Access Control are some of the IATM solutions used by corporations.
All the components mentioned above inside the IATM framework help the organization save costs, optimize software licensing requirements, and avoid contracting oversights from the vendors.
Built-in alerts help the asset management engineers to move towards procuring new licenses when the old ones are expiring. The alerts also allow them to track the laptops and desktops with older versions of OS and other applications installed. All these measures ensure legal compliance and avoid security breaches.